 |
||||
  |
    |
|||
|
||||
|
So given this fact, can you trust an automated cleaning routine provided by an anti-malware vendor? It depends on what is on your system, network, and all the other places your computer touches. If the system is one your kids use to play games, your private personal information isn't at risk. If you maintain your financial records and have other important personal information on it or use that system to connect to your bank account, this is a significant risk. If this is a system in your company, you'll want to seriously wipe and re-install, plus check other systems for problems and check your network traffic for malicious data. This started off as a self-educational challenge / research project -- "Can I clean this?" and I found too much knowledge to not share it with the world. I hope this helps you. If you find you might need assistance, you can reach me via the Contact link on the top left of this page. This is a long, detailed article, broken into a few sections: Initial infection
|
||||
|
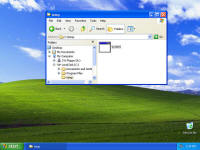
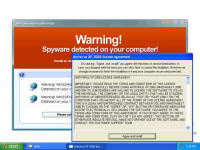
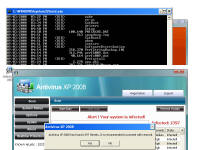
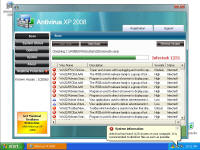
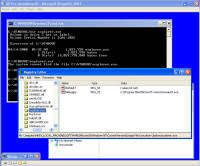
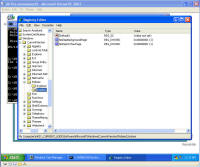
Enough background - show me the malware! Each of these screen shots can be clicked to bring up a larger version. All were taken from a Virtual PC window running Windows XP Service Pack 3 and fully patched as of early September 2008. Networks sniffs were taken with Wireshark running on the host PC. This shows the system just before infection. System.exe was created by the malicious site and somehow executed. I tried to replicate the drive-by download scenario but the site hosting the initial infection had already been cleaned. On the originally infected system, there were a few copies of this file with various extensions and names, telling me the system tried multiple ways to make the download and run happen. One was a screen saver, one was a media file, a .tmp file, and others. Once run, the background changed to a static graphic image and the window asking you if you accept the license agreement kept popping up. The license says you can indicate you don't agree, however there is no button to press to actually decline and the window won't let you move it off the screen. I moved the window around so you can see the scary warning about your system being infected. The rest of the background graphic -- I couldn't get a full screen shot because the dialogue box you have to agree to won't disappear. The text reads: "Warning! Win32/Adware.Virtumonde Detected on your
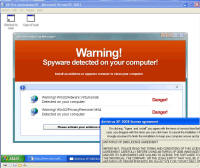
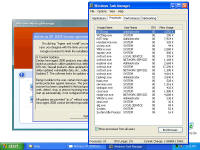
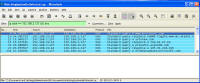
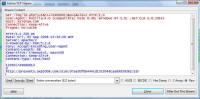
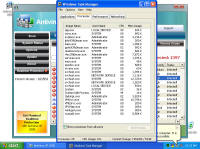
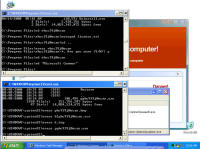
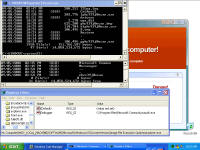
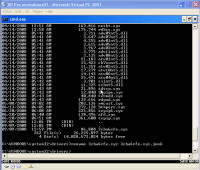
computer Danger!" As you will see, while there is certainly a LOT of danger from this malware those are just meant to scare you into buying their "Antivirus XP 2008" product. If you do buy it, I'll bet you get more crap or just get rid of that message -- but your system will remain infected with this or worse. There is probably also an "Antivirus XP 2009" out there now, and who knows but I'll bet they come out with "Antivirus XP 2010" For this particular version of the infection, a number of processes were started. This next screen shot shows processes named .tt7B.tmp, rld77.tmp, VMSrvc.exe, VMUSrvc.exe are the ones we can initially see. But trust me, there are others (plus, who knows what else this initial malware downloading application will download and install?) Upon asking the Antivirus product to scan my system, it pronounced that "Antivirus XP 2008 has found 1397 threats. It is recommended to proceed with removal." Curiously, this was the EXACT same number of threats found on the client computer I'd disinfected. What happened behind the scenes of this infection? Upon running the malware, the first thing this program did was phone home. This short bit of data sniff shows two queries, one to axionaw.com and the other to axp2008.com: The data conversation between the target system and its home base redirects the browser to http://presents.axp2008.com/scan/07ae3bfbb444cd15c9548caa69d39362/16/ where the system gets the bigger malware payload. I tried it recently and the part after "/scan/" and all those numbers appears to be just a method of tracking who and what was downloaded, no doubt so the malware distributors can see what methods of infection are working better than others and thus tailor how they send out stuff to infect more people. The exact HTML conversation looks like this: I could show you more data how scan.exe comes into your system, but suffice to say you are already running a program that downloads and runs whatever the authors wanted you to run. As it is said, "If I can get you to run my program on your computer, it isn't your computer anymore!" But this looks so real -- how can you be sure it is malware and not a real antivirus product?I've got screen shots from their 'support' page, where it is a form for email support. No phone number, no legitimate company name, no other contact for support other than sending email through their form. Lets look at the registration info for the two domains the malware phoned home to, axp2008.com and axionaw.com. There is a utility on the internet called 'whois' that digs information about domains from various data sources. Doing whois queries on both domains I came up with (edited down for easier reading): --------------- The phone number is disconnected. I called the day after this domain registration was created. What is really curious is how quickly the malware was created, pointed at this domain, distributed via infected websites, and landed on consumer PCs. Now THAT is an effective distribution network! Looking at the other domain: Domain Name: AXIONAW.COM [Brief update, 3/2010: All these domains now point to privacyprotect.com - so whoever they are they decided to fly below the radar] Does anybody reading this think sending your credit card number to some anonymous website run by someone in Russia is a good idea? If you leave the system to do nothing, it goes to a screen saver that simulates a Blue Screen of Death (BSOD) followed by a reboot. The BSOD rotates what it displays, and this happens to be one of the screens I captured: Show me the cleaning! The following walk-through is presented for your informational purposes only. It is entirely possible that whatever malware bits installed by this site (or others that are associated with it) have changed what and how they work since this was detected (9/2/2008) and written (9/10/2008). That said, I certainly do hope this helps you either disinfect your own system because you have the same problems or perhaps gives you clues as to what you might look for given some other form of malware present on your system. [4/2010 update: Actually, I no longer recommend cleaning systems and haven't for quite awhile now. It is highly probable that even after you completely disinfect your system from what you can see, that other malware is still lurking around. The last thing you want to do is log into your bank account from such an infected machine. So be safe - take your data off, wipe the system clean, reinstall from known good media, and put your data back on. After you read this article, read this other article before you decide to try cleaning it or trusting any other cleaning product / service. Be safe. Keep your money in your own accounts.] This was a scan I ran just before cleaning, caught in the middle to show you the whole scary program before it comes up with its pop-up windows you can't seem to get rid of: With that screen running, call up task manager and get rid of the tasks that obviously don't belong, like lphc939j0ecan.exe, pphc939j0ecan.exe, rhcc39j0ecan.exe, VMSrvc.exe, VMUSrvc.exe, and any others. If you've got malware that respawns when killed, you should instead use Process Explorer from sysinternals (www.sysinternals.com, now owned by Microsoft) and suspend the processes instead of killing them: With those processes dead, I found those files and deleted them. In my case, they were in various directories, including: If you have this infection, those file names are likely randomized and thus different from the ones presented above. I found these by looking in the directories and sorting by date / time and looking at the latest files gave me most all of them in both the client and my deliberate laboratory infections. The following screen shots show the erasures in progress, along with the background screen that was left over by the malware to keep me quaking in my boots that my system was infected and I should buy their cleaning product.
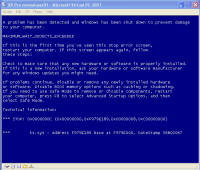
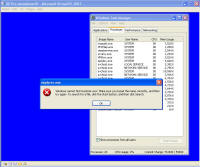
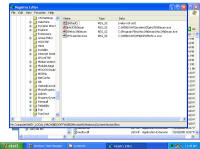
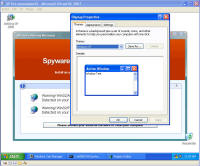
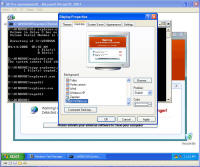
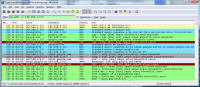
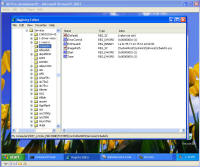
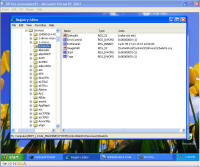
Remnants of damage left behind After all that cleaning, I was feeling pretty confident the system was cleaned from these threats and rebooted. This was the only screen I saw after the boot screen: It was a blank blue background screen with no toolbar, icons, or anything. Apparently one of the bits of malware I'd removed was somehow hooked into running some critical part of windows. I could hit Ctrl-Alt-Del and come up with task manager. Looking, I couldn't find explorer.exe running, so I tried running it manually. What came up was an error dialogue box stating that: "Windows cannot find 'explorer.exe'. Make sure you typed the name correctly, and then try again. To search for a file, click the Start button, and then click Search." The screen is captured here: I checked, and explorer was right where it should have been, was the right size, and I even copied a new copy from another system in case that program had been hacked by the malware, and still explorer would not start. Nor would it start from the command line. Somehow (rootkit?) that file was being redirected and not allowed to run. However, I could copy explorer.exe to explorer1.exe and then it ran just fine. That told me the binary was in tact, but it was somehow being mangled or redirected. Some strategic Internet searching lead me to a registry key that can be used to redirect one program to another for debugging purposes. That key's value is shown in the screen below and should be deleted. Having copied and now running explorer1.exe, I got the desktop, start bar, and other associated functionality back. In this screen, the key redirects explorer.exe to instead run the program at C:\Program Files\Microsoft Common\wuauclt.exe, which is their malware. As it turns out, there was still some traces of malware on the system that re-download and re-infected the system with the same malware I'd just removed ... so for me it was lather, rinse, and repeat what I'd already done. For reference, the key to delete was: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\explorer.exe\Debugger It looks like this key can be used to redirect just about any executable to another. Very powerful. But with great power comes great responsibility. The next step was getting rid of various files that were run upon startup. You can use the program autoruns, also available from sysinternals.com or check all the various run keys manually. As the screen shot below shows, I found them at HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run. The key VPCUserServices is needed for the virtual machine additions and is not part of the malware. There are a few remnants of damage left behind -- first off, that annoying screen telling me I'm infected. Being a background screen, it is in the background properties pages. Except the malware disabled the display properties and the screen saver tabs to keep its message displaying as long as possible. By using group policy settings, anyone can disable or enable your ability to do just about anything on your system. On the left, screen showing the Display Properties control panel's Display and Screen Saver tabs are missing. On the right are the registry keys that were created to disable them. So deleting the registry keys: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System\NoDispBackgroundPage Brings your Screen Saver and Display tabs back from the "Display Properties" control panel dead: And you can now change them off that awful malware reminder and onto something more pleasant. And so I thought I was done. Yet again. Are you sensing a pattern here? No matter how much you do, you can never really be 100% certain that every trace of the malware is gone -- unless you completely wipe out the system and reinstall everything from known good media. Again I thought I was done, and again I was wrong. As it turns out, that system was phoning home and sending out spam mail. Here are some network sniff traces I took while experimenting with it. The was a fresh boot in the virtual machine. I'm giving the packet number, followed by what is happening. 212-217: Check for internet connectivity, connect / disconnect from
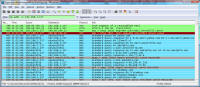
google.com. If no internet, it stops. I found this by booting first with no internet connectivity, then full connectivity, then I added a rule to the firewall to prevent this system from sending any SMTP mail packets which I could instantly turn on / off. Once it phoned home and got its payload, it started spamming and I could shut down SMTP and watch all the connections get blocked at my local firewall. Packets 228-401 are split between the two sniff snapshots and are the malware logging into its home base, getting its spam mail messages, who to send the mail to, and then starting to connect to different mail servers to actually send. Packets 398-420 are here: I grabbed one of the message sequences that got out of the system to show the spam mail: I dug around with various tools for an hour or so looking for this piece of code. TCPView showed a process as a system service generating all the connections, but that system service had two very legitimate uses (the Event Log and the Plug and Play service). The DNS Cache service was doing a lot, but that was in response to the malware making DNS queries to find mail servers. Nothing showed up in any of the autoruns, process monitor, or any other tool as a 'this is the malware you are looking for' since it was somehow hiding. When I started poking around in system drivers, I found one I couldn't recognize and was date / time stamped at the infection time, which I also couldn't delete as it appeared like it was in use. That file was 3cba6cfe.sys and is pictured below. As it turns out, I booted into safe mode and could see I wasn't sending any malware, and thus could rename the suspected malware, which I'm doing below: Once renamed, I booted back into normal windows mode and watched the sniffer -- no queries were made, no connections out to the bad site happened, and all appeared quiet on the network, so I'm thinking this was the bad stuff. That spam sending malware was actually a driver or service starting up in the registry in a couple of places called "3cba6cfe.sys" (though if you see it the name is probably different by now) -- those two places are shown in the two screens below. Both keys were deleted with the registry editor: I watched the system for a few more hours and didn't see any more bad network data, so I pronounced this re-infected virtual machine as reasonably clean and deleted it. But I wouldn't bet my life savings on it being 100% clean -- it could have had still more hidden stuff that only wakes up if I log into my bank, and only then forward my login information to someone else interested in cleaning my account. How would you like to make it so you never have to go through this again? Read this article on making malware recovery easy! ------ If you found this helpful (or not), please send me a brief email -- one line
will more than do. If I see people need, want, and / or use this kind of
information that will encourage me to keep creating this kind of content.
Whereas if I never hear from anyone, then why bother? David Soussan (C) 2008, 2010 DAS Computer Consultants, LTD. All Rights Reserved.
The following items below this line are for search engines to assist them in indexing this content. Malware |
||||